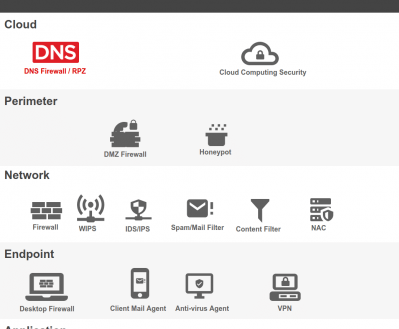
Proper cybersecurity begins with layers and monitoring the DNS layer will give you a better position for insuring a healthy and safe network. Here are 5 actions you can take to improve your security profile.

New Feature: Easy Active Directory Based Policies
I am pleased to announce that we have launched our Active Directory (AD)-based group policy integration, giving ScoutDNS admins more options for policy deployment. What